- Summary
- Retrieve Issuer Public key Modulus
- Get RID
- Get CA public key index and CA
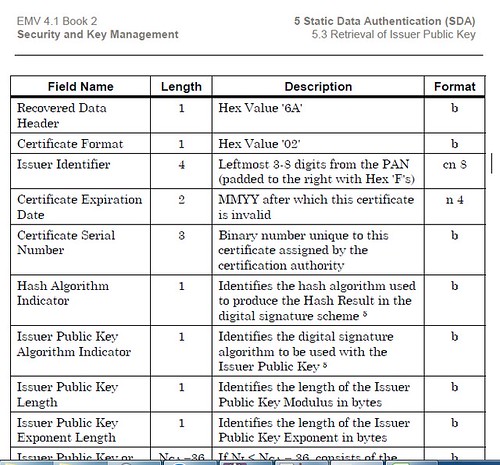
- Retrieval of Issuer Public Key
- Verify SSAD
- Decrypt SSAD
- Verify SSAD
- Reference
Summary
Test the Open Smart Card Shell on “doemv.js” on credit card for the EMV SDA function, get into the detail to understand the EMV SDA procedure steps.
The Certification Authority Public Key (PCA) is stored in the IC Terminal. PCA will be used to decrypt Issuer PK Certificate, and to extracts the P1 key (Issuer Public Key). P1 key will be used to decrypt the SSAD (Signed Static Application Data).
Refer to below EMV v4.3 Book 2 - EMVCo SDA flow (Chapter 5: 5 Static Data Authentication (SDA) page 51).

I tested with below reader and expired credit card.

Expired Credit Card.

Retrieve Issuer Public key Modulus
Get RID
To get Application Provider Identifier (RID), we extract the first five bytes of the Application Identifier (AID). In the test it is:A000000003 (Visa)
Get CA public key index and CA
Then read the Certification Authority Public Key Index from the ICC, the index can be read out through tag 8F (Certification Authority Public Key Index). In the test, the index is 0x08. It indicates below CA.
d.addSchemePublicKey(new ByteString("A000000003", HEX), 8, new Key("schemepublickeys/kp_visa_1408_08.xml"));The CA value is:
D9FD6ED75D51D0E30664BD157023EAA1FFA871E4DA65672B863D255E81E137A51DE4F72BCC9E44ACE12127F87E263D3AF9DD9CF35CA4A7B01E907000BA85D24954C2FCA3074825DDD4C0C8F186CB020F683E02F2DEAD3969133F06F7845166ACEB57CA0FC2603445469811D293BFEFBAFAB57631B3DD91E796BF850A25012F1AE38F05AA5C4D6D03B1DC2E568612785938BBC9B3CD3A910C1DA55A5A9218ACE0F7A21287752682F15832A678D6E1ED0B
Retrieval of Issuer Public Key
Decrypt the Issuer PK Certificate with CA to get issuer public key, both Issuer PK Certificate and CA should be the same length, in the test, the length is 176 bytes.
Issuer PK Certificate with CA can be retrieved from tag 90.
6751D5FE447XXXXXX…
Also need the Issuer Public Key Remainder, it can be retrieved from tag 92.
CCE4335A1XXXX….
Refer to below EMV v4.3 Book 2 - EMVCo SDA flow (5.3 Retrieval of Issuer Public Key page 59).
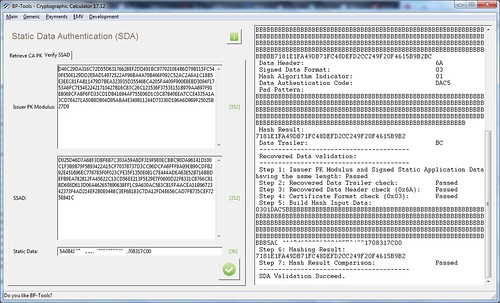
Use BP-Tools - Cryptographic Calculator to verify as below,

After decryption, go through 12 steps to verify the result, as below,
Step 1: CA PK Modulus and Issuer’s Public Key Certificate having the same size: Passed
Step 2: Recovered Data Trailer check: equal to ‘BC’, Passed
Step 3: Recovered Data Header check (0x6A): Passed
Step 4: Certificate Format check (0x02): Passed
Step 5: Hash Input Data is as below,
Data Format + Issuer Identifier + Certificate Expiration Date + Certificate Serial Number + Hash Algorithm Indicator + Issuer Public Key Algorithm Indicator + Issuer Public Key Length + Issuer Public Key Exponent Length + Issuer Public Key + Issuer Public Key Remainder + Issuer public key exponent, in the test,
02414746FF1221033E130101B001D46C29DA316C72D55D63176628EF2DD491BC9770210E4B6D79B115FC540FE50E129DD2E9AD14972522AF96BA4A70B466F092C52AC2A6A1C18B5E3EEC81FAB11479D7BEA323935D355468CA205FA409F900E8EBD3094F1753A6FC7E54E22421710427B16C83C26C123536F3753E151B979AA697F91E8069CFABF6FD33CD1DB41694AF755E06D1C0C87840EEA7CCE4335A1A3CD7E4271A50B8D804D95ABA4E349811244D73336D196A6D969F25025B27D903
Step 6: Hashing Result:
Use SHA-1 Hash to calculate the hash result.
D553BF6A78E42CDEF6C9ECD0B74F64C42883615A
Step 7: Hash Result Comparison: Passed
Step 8: Issuer Identifier check: Skipped (DIY)
Step 9: Certificate Expiry Date check: Passed
Step 10: RID revocation check: Skipped (optional DIY)
Step 11: PK Algorithm Indicator check: Passed
Step 12: Issuer Public Key Modulus:
Issuer Public Key Modulus is Issuer Public Key + Issuer Public Key Remainder.
In the test:
D46C29DA316C72D55D63176628EF2DD491BC9770210E4B6D79B115FC540FE50E129DD2E9AD14972522AF96BA4A70B466F092C52AC2A6A1C18B5E3EEC81FAB11479D7BEA323935D355468CA205FA409F900E8EBD3094F1753A6FC7E54E22421710427B16C83C26C123536F3753E151B979AA697F91E8069CFABF6FD33CD1DB41694AF755E06D1C0C87840EEA7CCE4335A1A3CD7E4271A50B8D804D95ABA4E349811244D73336D196A6D969F25025B27D9
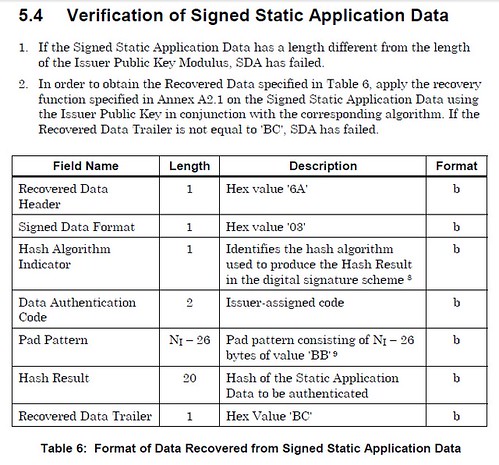
Verify SSAD
Decrypt SSAD
Decrypt the Signed Application Data (SSAD) by using the Issuer Public Key Modulus retrieved from above steps.
The SSAD (Signed Static Application Data) is retrieved from tag 93.
Another input is Static Data. It is the data to be authenticated, for the test, it includes the Application Primary Account Number (PAN) and Application Expiration Date. It reads 5A0841474630XXXXXXXX5F2403170831.
Static Data also includes the Static Data Authentication Tag List (Tag 9F4A), here the value is 0x82. 0x82 value was read through GET PROCESSING OPTIONS Command (80A8), first two bytes is Application Interchange Profile (AIP), tag 0x82, value here is 7C00.
So the Static Data to be authenticated is
5A0841474630XXXXXXXX5F24031708317C00
Verify SSAD
After decryption, go through 7 steps to verify the SSAD.
Refer to below EMV v4.3 Book 2 - EMVCo SDA flow (5.4 Verification of Signed Static Application Data, page 61).
Step 1: Issuer PK Modulus and Signed Static Application Data having the same length: 176 bytes, Passed
Step 2: Recovered Data Trailer check: 0xBC Passed
Step 3: Recovered Data Header check (0x6A): Passed
Step 4: Certificate Format check (0x03): Passed
Step 5: Build Hash Input Data
Signed Data Format + Hash Algorithm Indicator + Data Authentication Code + Pad Pattern + Static Data to be authenticated
0301DAC5BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB5A0841474630XXXXXXXX5F24031708317C00
Step 6: Hashing Result: 7181E1FA49DB71FC48DEFD2CC249F20F4615B9B2
Step 7: Hash Result Comparison:
Use SHA-1 Hash to calculate the hash result.
Use BP-Tools - Cryptographic Calculator to verify as below,
Reference
Open Smart Card Shell Static Data Authentication (SDA)
Test SHA-1 Hash
Open Smart Card Shell Test on dump.js
Github scsh-scripts/emv/doemv.js
BP-Tools - Cryptographic Calculator
EMV_v4.3_Book_3_Application_Specification - EMVCo
EMV v4.3 Book 2 - EMVCo