文章目录
- Summary
- Reader and Passport
- MRZ-based Basic Access Control Authentication
- Mutual authentication - Terminal to card
- Mutual authentication - Card response to terminal.
- Secure Messaging
- Test with dumpmrtd.js
- Check digit
- Reading passport using PassportReader
- Reference
Summary
Studied the ICAO spec, tested Biometric Passport (MRTD) reading with my own passport. Successfully did the BAC (Basic Access Control) authentication to my passport and read out the basic passport information, including: EF_COM (1E), EF_DG1, EF_DG2 (Face) information. Analyzed the detail.
Reader and Passport
Tested with below Omnikey 5321v2 reader.

My own passport, can see the Antenna and chip clearly under the flashlight.

MRZ-based Basic Access Control Authentication
Refer to ICAO doc 9303 part 1 volume 2, Terminal and Passport will do mutual authentication, below are real data,
Select AID:
00A4040407A000000247100100
6210820138830201008407A00000024710019000
Generate an 8 byte random and a 16 byte random RND.IFD from terminal:
0084000008
9E231AF7C3A191AD9000
Mutual authentication has below two APDU commands,
0082000028DC1DF138CD8D0492DA04458328C965A00AF47808D9E9C04515DEB2E93AF96AA4B15E3AB4A224E89300
3983270AADE2C6841E358D626CF6757135AFF376548C250D954F4BF07E2D643081F964E0E9BE660D9000
Mutual authentication - Terminal to card
============================
Hash Input : E5648030E680061232006246
MRZHash (Sha 1): 561754EE47DA4256C15FE4F40A17639CB75F4C26
First 16 bytes: 561754EE47DA4256C15FE4F40A17639C + 00000001 = 561754EE47DA4256C15FE4F40A17639C00000001
Result for sha1: eb0f20e35df29c76ecd3ef574bc74a1d4781ee46
ValueofKey Kenc: EB0F20E35DF29C76ECD3EF574BC74A1DHash Input : E5648030E680061232006246
MRZ Hash : 56 17 54 EE 47 DA 42 56 C1 5F E4 F4 0A 17 63 9C B7 5F 4C 26
First 16 bytes: 561754EE47DA4256C15FE4F40A17639C + 00000002 = 561754EE47DA4256C15FE4F40A17639C00000002
6dc37b571c8e53dd1beab6e7cb4185ec49391abc
Value of Key Kmac : 6D C3 7B 57 1C 8E 53 DD 1B EA B6 E7 CB 41 85 EC
6DC37B571C8E53DD1BEAB6E7CB4185ECPlain Block : 7F 37 6D 71 35 60 3F EB 9E 23 1A F7 C3 A1 91 AD 57 3B C4 51 80 D9 58 6A A9 A7 A8 5B 55 E8 35 8A
7F376D7135603FEB9E231AF7C3A191AD573BC45180D9586AA9A7A85B55E8358A
RND.IFD + RND.ICC + KIFD = 7F376D7135603FEB + 9E231AF7C3A191AD + 573BC45180D9586AA9A7A85B55E8358A
KIFD = 573BC45180D9586AA9A7A85B55E8358A
Encytpted by Kenc (EB0F20E35DF29C76ECD3EF574BC74A1D) 3DES-CBC the result is: DC1DF138CD8D0492DA04458328C965A00AF47808D9E9C04515DEB2E93AF96AA4Cryptogram : DC 1D F1 38 CD 8D 04 92 DA 04 45 83 28 C9 65 A0 0A F4 78 08 D9 E9 C0 45 15 DE B2 E9 3A F9 6A A4
DC1DF138CD8D0492DA04458328C965A00AF47808D9E9C04515DEB2E93AF96AA4
SSC = C3 A1 91 AD 35 60 3F EB
C3A191AD35603FEBDC1DF138CD8D0492DA04458328C965A00AF47808D9E9C04515DEB2E93AF96AA4 calculate MAC by Kmac (6DC37B571C8E53DD1BEAB6E7CB4185EC)
Initial IV: 0000000000000000, no padding, ISO 9797 Algorithm 3 (Card IDE MAC button), the result is: B15E3AB4A224E893MAC : B1 5E 3A B4 A2 24 E8 93Sending commands to card: 0082000028DC1DF138CD8D0492DA04458328C965A00AF47808D9E9C04515DEB2E93AF96AA4B15E3AB4A224E893
============================
Mutual authentication - Card response to terminal.
============================
Calculate the respongse from card,
3983270AADE2C6841E358D626CF6757135AFF376548C250D954F4BF07E2D6430 81F964E0E9BE660D
3983270AADE2C6841E358D626CF6757135AFF376548C250D954F4BF07E2D6430 calculate MAC by Kmac (6DC37B571C8E53DD1BEAB6E7CB4185EC)
Initial IV: 0000000000000000, no padding, ISO 9797 Algorithm 3 (Card IDE MAC button), the result is: 81F964E0E9BE660D3983270AADE2C6841E358D626CF6757135AFF376548C250D954F4BF07E2D6430 decrypt by Kenc (EB0F20E35DF29C76ECD3EF574BC74A1D) 3DES-CBC the result is:
9E231AF7C3A191AD7F376D7135603FEBA6E76A1CE30595F1AFA5B3ADE80E54FF9E231AF7C3A191AD7F376D7135603FEBA6E76A1CE30595F1AFA5B3ADE80E54FF =
RND.ICC + RND.IFD + KICC
9E231AF7C3A191AD + 7F376D7135603FEB + A6E76A1CE30595F1AFA5B3ADE80E54FF
KICC = A6E76A1CE30595F1AFA5B3ADE80E54FFKenc : A9 A5 38 46 BB AD 5D 9F DF E2 5B 58 16 DE 05 AD
Kmac : BA 0C 8B 9F A6 41 87 67 1A 0A 1D B8 CD CD 65 AAKIFD = 573BC45180D9586AA9A7A85B55E8358A
KICC = A6E76A1CE30595F1AFA5B3ADE80E54FF
KIFD XOR KICC = f1dcae4d63dccd9b06021bf6bde66175f1dcae4d63dccd9b06021bf6bde6617500000001 Sha 1 = a9a53846bbad5d9fdfe25b5816de05adfbca9a8a
f1dcae4d63dccd9b06021bf6bde6617500000002 sha 1 = ba0c8b9fa64187671a0a1db8cdcd65aa957dcb19Kenc = a9a53846bbad5d9fdfe25b5816de05ad
Kmac = ba0c8b9fa64187671a0a1db8cdcd65aa
SSC = C3A191AD35603FEB
============================
SSC = Send Sequence Counter
RND.IFD = 7F376D7135603FEB
RND.ICC = 9E231AF7C3A191AD
SSC = RND.ICC ( 4 least significant bytes) || RND.IFD ( 4 least significant bytes)
Here SSC = C3A191AD35603FEB.
SSC will increase by 1 after each command.
Secure Messaging
Refer to ICAO doc 9303 part 1 volume 2, the communication between terminal and passport went through the secure channel, encrypted by Kenc and MAC authenticated by Kmac. Read out the basic passport information, including: EF_COM (1E), EF_DG1, EF_DG2 (Face) information. Analyzed the detail.
============================
Reading EF_COM (1E)...Command header: 0CB09E0080000000
Build DO'97' DO97 = ‘970104’
0CB09E0080000000970104
SSC = C3A191AD35603FEB
Increment SSC with 1:
SSC = C3A191AD35603FECConcatenate SSC and M and add padding:
C3A191AD35603FEC0CB09E00800000009701048000000000
Calculate MAC ISO 9797 Algorithm 3,
MAC CC = 4DB9C9B0CCCB06C7Build DO‘8E’: DO8E = ‘8E084DB9C9B0CCCB06C7’Construct and send protected APDU:
0CB09E00XX + 970104 + 8E084DB9C9B0CCCB06C7 = 0CB09E000D9701048E084DB9C9B0CCCB06C7Receive response APDU of MRTD’s chip: 87090185481C85605B066F990290008E085BA9A1FA2EC524D39000Verify RAPDU CC by computing MAC of concatenation DO‘87’ and DO‘99’:Increment SSC with 1:
SSC = C3A191AD35603FEDConcatenate SSC, DO‘87’ and DO‘99’ and add padding:C3A191AD35603FED + 87090185481C85605B066F99029000 = C3A191AD35603FED87090185481C85605B066F99029000Compute: MAC with KmacC3A191AD35603FED87090185481C85605B066F99029000 use Kmac = ba0c8b9fa64187671a0a1db8cdcd65aa, ISO 9797 algorithm 3 padding 8000.., the result is: 5BA9A1FA2EC524D3It is matching 8E085BA9A1FA2EC524D3Decrypt data of DO‘87’ with Kenc(a9a53846bbad5d9fdfe25b5816de05ad)
85481C85605B066F
Result as below:
60165F0180000000Determin the length of the structure: 0x16 + 2 = 24 = 0x18
============================0CB09E000D9701048E084DB9C9B0CCCB06C700
87090185481C85605B066F990290008E085BA9A1FA2EC524D39000//60165F0104303130375F36063034303030305C046175636D//615B5F1F58504153475058494F4E473C3C4855494C494E3C3C3C3C3C3C3C3C3C3C3C3C3C3C3C3C3C3C3C3C3C3C3C3C3C3C45353634383033304536534750383030363132334D323030363234365338303633303939493C3C3C3C3C3932Encrypted: 5B2D2273260E61D993E401BAE9B8500F135AEEE745E6EC2DBF24797D8ADFF3E3C6D1A30731C463528A42E96EBE329BD779B6A31AFB18DCC67924FFC0D0786D7E532C0E0C36A631877AD6D4FE4C5C80FF97757E4219FE0AA20A2E26564CB40981============================
Command header: 0CB09E0080000000
Build DO'97' DO97 = ‘970118’
0CB0000080000000970118
SSC = C3A191AD35603FED
Increment SSC with 1:
SSC = C3A191AD35603FEEConcatenate SSC and M and add padding: Kmac = ba0c8b9fa64187671a0a1db8cdcd65aa
C3A191AD35603FEE0CB00000800000009701188000000000
Calculate MAC ISO 9797 Algorithm 3,
MAC CC = 47239CEA4C98F032Build DO‘8E’: DO8E = ‘8E0847239CEA4C98F032’Construct and send protected APDU:
0CB00000XX + 970118 + 8E0847239CEA4C98F032 = 0CB000000D9701188E0847239CEA4C98F032Receive response APDU of MRTD’s chip: 872101A1991A4B6DFB8E662F95A7AFFB67ADF4D96B22094862365AA282E280243B1A8A990290008E082D40C635C29A208B9000Verify RAPDU CC by computing MAC of concatenation DO‘87’ and DO‘99’:Increment SSC with 1:
SSC = C3A191AD35603FEFConcatenate SSC, DO‘87’ and DO‘99’ and add padding:C3A191AD35603FEF + 872101A1991A4B6DFB8E662F95A7AFFB67ADF4D96B22094862365AA282E280243B1A8A99029000 =
C3A191AD35603FEF872101A1991A4B6DFB8E662F95A7AFFB67ADF4D96B22094862365AA282E280243B1A8A99029000Compute: MAC with KmacC3A191AD35603FEF872101A1991A4B6DFB8E662F95A7AFFB67ADF4D96B22094862365AA282E280243B1A8A99029000 use Kmac = ba0c8b9fa64187671a0a1db8cdcd65aa, ISO 9797 algorithm 3 padding 8000.., the result is: 2D40C635C29A208BIt is matching 8E082D40C635C29A208BDecrypt data of DO‘87’ with Kenc(a9a53846bbad5d9fdfe25b5816de05ad)
A1991A4B6DFB8E662F95A7AFFB67ADF4D96B22094862365AA282E280243B1A8A
Result as below:
60165F0104303130375F36063034303030305C046175636D8000000000000000============================0CB000000D9701188E0847239CEA4C98F03200
872101A1991A4B6DFB8E662F95A7AFFB67ADF4D96B22094862365AA282E280243B1A8A990290008E082D40C635C29A208B9000Below
Increment SSC with 1:
SSC = C3A191AD35603FF0
SSC = C3A191AD35603FF10CB081000D9701048E08ED4C0341554B38E600
8709017175822DC98CD038990290008E0893F55DE41E6A2F859000Below
Increment SSC with 1:
SSC = C3A191AD35603FF2
SSC = C3A191AD35603FF30CB000000D97015D8E08D0C0FBDDA5C3B54100
8761015B2D2273260E61D993E401BAE9B8500F135AEEE745E6EC2DBF24797D8ADFF3E3C6D1A30731C463528A42E96EBE329BD779B6A31AFB18DCC67924FFC0D0786D7E532C0E0C36A631877AD6D4FE4C5C80FF97757E4219FE0AA20A2E26564CB40981990290008E083B909990D71B515C9000Increment SSC with 1:SSC = C3A191AD35603FF4
SSC = C3A191AD35603FF5M = ‘0CB0820080000000970104’Concatenate SSC and M and add padding:C3A191AD35603FF4 + 0CB0820080000000970104 = C3A191AD35603FF40CB0820080000000970104 use Kmac = ba0c8b9fa64187671a0a1db8cdcd65aa, ISO 9797 algorithm 3 padding 8000.., the result is: 43E75A396B61B15BC3A191AD35603FF5 + 870901CC079A7C64695A6099029000
=
C3A191AD35603FF5870901CC079A7C64695A60990290007DDDF1DA354269940CB082000D9701048E0843E75A396B61B15B00
870901CC079A7C64695A60990290008E087DDDF1DA354269949000
Decrypt data of DO‘87’ with Kenc(a9a53846bbad5d9fdfe25b5816de05ad)
Decrypted: 758230F480000000Increment SSC with 1:
SSC = C3A191AD35603FF6
SSC = C3A191AD35603FF7M = ‘0CB00000800000009701DF’Concatenate SSC and M and add padding:C3A191AD35603FF6 + 0CB00000800000009701DF8000000000 = C3A191AD35603FF60CB00000800000009701DF8000000000 use Kmac = ba0c8b9fa64187671a0a1db8cdcd65aa, ISO 9797 algorithm 3 padding 8000.., the result is: 6297989870DB71B2Concatenate SSC, DO‘87’ and DO‘99’ and add padding:C3A191AD35603FF7 + 8781E10172A4814D10CE3967348DCF7611B2BDB43303C33DF1F047527A96D83852E2A58DCA582B09B506D3A6B47F51029081D50B5A5892B1D731DC1F230F79FF4F0361B2FED69D67784196E1E8ACF3176D1C76D6818B822734B3360657C4ABE2276BF4991F329FA14D5798F67E7978BFE845FD34C9DD410042C5A6E79F74CA6CCB4B51869542251CEDD22483D8F8BFCDEFB55F530692BD4502D825653A46F1C517D2DF882B5AEC890DCCC9470971E6F1A125F0FCECDF97A9105339D6841A49964D70378FA02A522AEA2AD4025AA5E3CF681B75395DECECF7217D91BE3687E1EE70B486EA99029000
=
C3A191AD35603FF78781E10172A4814D10CE3967348DCF7611B2BDB43303C33DF1F047527A96D83852E2A58DCA582B09B506D3A6B47F51029081D50B5A5892B1D731DC1F230F79FF4F0361B2FED69D67784196E1E8ACF3176D1C76D6818B822734B3360657C4ABE2276BF4991F329FA14D5798F67E7978BFE845FD34C9DD410042C5A6E79F74CA6CCB4B51869542251CEDD22483D8F8BFCDEFB55F530692BD4502D825653A46F1C517D2DF882B5AEC890DCCC9470971E6F1A125F0FCECDF97A9105339D6841A49964D70378FA02A522AEA2AD4025AA5E3CF681B75395DECECF7217D91BE3687E1EE70B486EA99029000here need to pad 8000000000000000 as belowC3A191AD35603FF78781E10172A4814D10CE3967348DCF7611B2BDB43303C33DF1F047527A96D83852E2A58DCA582B09B506D3A6B47F51029081D50B5A5892B1D731DC1F230F79FF4F0361B2FED69D67784196E1E8ACF3176D1C76D6818B822734B3360657C4ABE2276BF4991F329FA14D5798F67E7978BFE845FD34C9DD410042C5A6E79F74CA6CCB4B51869542251CEDD22483D8F8BFCDEFB55F530692BD4502D825653A46F1C517D2DF882B5AEC890DCCC9470971E6F1A125F0FCECDF97A9105339D6841A49964D70378FA02A522AEA2AD4025AA5E3CF681B75395DECECF7217D91BE3687E1EE70B486EA990290008000000000000000use Kmac = ba0c8b9fa64187671a0a1db8cdcd65aa, ISO 9797 algorithm 3 padding 8000.., the result is: 49AB27C48C7E639A0CB000000D9701DF8E086297989870DB71B200
8781E10172A4814D10CE3967348DCF7611B2BDB43303C33DF1F047527A96D83852E2A58DCA582B09B506D3A6B47F51029081D50B5A5892B1D731DC1F230F79FF4F0361B2FED69D67784196E1E8ACF3176D1C76D6818B822734B3360657C4ABE2276BF4991F329FA14D5798F67E7978BFE845FD34C9DD410042C5A6E79F74CA6CCB4B51869542251CEDD22483D8F8BFCDEFB55F530692BD4502D825653A46F1C517D2DF882B5AEC890DCCC9470971E6F1A125F0FCECDF97A9105339D6841A49964D70378FA02A522AEA2AD4025AA5E3CF681B75395DECECF7217D91BE3687E1EE70B486EA990290008E0849AB27C48C7E639A900072A4814D10CE3967348DCF7611B2BDB43303C33DF1F047527A96D83852E2A58DCA582B09B506D3A6B47F51029081D50B5A5892B1D731DC1F230F79FF4F0361B2FED69D67784196E1E8ACF3176D1C76D6818B822734B3360657C4ABE2276BF4991F329FA14D5798F67E7978BFE845FD34C9DD410042C5A6E79F74CA6CCB4B51869542251CEDD22483D8F8BFCDEFB55F530692BD4502D825653A46F1C517D2DF882B5AEC890DCCC9470971E6F1A125F0FCECDF97A9105339D6841A49964D70378FA02A522AEA2AD4025AA5E3CF681B75395DECECF7217D91BE3687E1EE70B486EA
Decrypted as: Decrypt data of DO‘87’ with Kenc(a9a53846bbad5d9fdfe25b5816de05ad)
758230F47F618230EF0201017F608230E7A10F8002010181010287020101880200085F2E8230D14641430030313000000030D10001000030C300000000000000000000000000000000010100F001400100000000000000000C6A5020200D0A870A00000014667479706A703220000000006A7032200000002D6A703268000000166968647200000140000000F00003070701000000000F636F6C7201000000000010000000006A703263FF4FFF51002F0000000000F0000001400000000000000000000000F00000014000000000000000000003070101070101070101FF5280Increment SSC with 1:
SSC = C3A191AD35603FF8
SSC = C3A191AD35603FF9M = ‘0CB00000800000009701DF’Concatenate SSC and M and add padding:C3A191AD35603FF8 + 0CB000DF800000009701DF8000000000 = C3A191AD35603FF80CB000DF800000009701DF8000000000 use Kmac = ba0c8b9fa64187671a0a1db8cdcd65aa, ISO 9797 algorithm 3 padding 8000.., the result is: ACB1BCA310AB9749C3A191AD35603FF9 + 8781E101A800E2FF06DC941C5D0CDD4C92B7A8883DE3FCF197072C90639660984D624F2146361FC15762C3DD986185AB42153CA5B7D4ED38767DBF7DF215D67B36CBCB4CF43EA44C3C09C2A68BAE04AC6DA90F6660E93729C920908AECAA72397869CAB7423CEF3DC6F62FE706CCBEE703A80998B599A887ACDF2404AB1E71A9488D54E392232AB1B17578ACC6572494B9725897B35AE4B6DAE29DD61CDE16FE895AA920EFC0BF7747E697D81CFDCB2645D2BA39A0A7821B7E00D5B9E3E3F105F9A92DB374760D4E6B89AF84427702530B6FF6209FAF6CCDBFAFD16AD47B3EF6EC87478099029000
=C3A191AD35603FF98781E101A800E2FF06DC941C5D0CDD4C92B7A8883DE3FCF197072C90639660984D624F2146361FC15762C3DD986185AB42153CA5B7D4ED38767DBF7DF215D67B36CBCB4CF43EA44C3C09C2A68BAE04AC6DA90F6660E93729C920908AECAA72397869CAB7423CEF3DC6F62FE706CCBEE703A80998B599A887ACDF2404AB1E71A9488D54E392232AB1B17578ACC6572494B9725897B35AE4B6DAE29DD61CDE16FE895AA920EFC0BF7747E697D81CFDCB2645D2BA39A0A7821B7E00D5B9E3E3F105F9A92DB374760D4E6B89AF84427702530B6FF6209FAF6CCDBFAFD16AD47B3EF6EC87478099029000
here need to pad 8000000000000000 as below
C3A191AD35603FF98781E101A800E2FF06DC941C5D0CDD4C92B7A8883DE3FCF197072C90639660984D624F2146361FC15762C3DD986185AB42153CA5B7D4ED38767DBF7DF215D67B36CBCB4CF43EA44C3C09C2A68BAE04AC6DA90F6660E93729C920908AECAA72397869CAB7423CEF3DC6F62FE706CCBEE703A80998B599A887ACDF2404AB1E71A9488D54E392232AB1B17578ACC6572494B9725897B35AE4B6DAE29DD61CDE16FE895AA920EFC0BF7747E697D81CFDCB2645D2BA39A0A7821B7E00D5B9E3E3F105F9A92DB374760D4E6B89AF84427702530B6FF6209FAF6CCDBFAFD16AD47B3EF6EC874780990290008000000000000000MAC result is as: 060D0A8A5145227D0CB000DF0D9701DF8E08ACB1BCA310AB974900
8781E101A800E2FF06DC941C5D0CDD4C92B7A8883DE3FCF197072C90639660984D624F2146361FC15762C3DD986185AB42153CA5B7D4ED38767DBF7DF215D67B36CBCB4CF43EA44C3C09C2A68BAE04AC6DA90F6660E93729C920908AECAA72397869CAB7423CEF3DC6F62FE706CCBEE703A80998B599A887ACDF2404AB1E71A9488D54E392232AB1B17578ACC6572494B9725897B35AE4B6DAE29DD61CDE16FE895AA920EFC0BF7747E697D81CFDCB2645D2BA39A0A7821B7E00D5B9E3E3F105F9A92DB374760D4E6B89AF84427702530B6FF6209FAF6CCDBFAFD16AD47B3EF6EC874780990290008E08060D0A8A5145227D9000
......
Test with dumpmrtd.js
Refer to Open SmartCard Biometric Passport (MRTD) with Logical Data Structure (LDS), it’s easy to use the js script dumpmrtd.js to readout passport detail information.
/** Read file from passport and save to disk**/
function handleFile(secureChannel, lds, name, fid) {
print("Reading " + name + " (" + fid + ")...");// Select filevar ef = new CardFile(lds, ":" + fid);if (secureChannel) {
// Set secure channel as credential for read accessef.setCredential(CardFile.READ, Card.ALL, secureChannel);}// Read first 4 bytes of filevar res = ef.readBinary(0, 4);print("Reading 1st 4 bytes: " + res);// Determine file length from TLV headervar len = lengthFromHeader(res);print("Length is: " + len);// Read complete filevar res = ef.readBinary(0, len);print("Content");print(res);writeFileOnDisk(name + ".bin", res);return res;
}The result is as below,
>load("scsh-scripts-master/icao/dumpmrtd.js")
Trying BAC with MRZ2=E5648030E6SGP8006123M2006246S8063099I<<<<<92
Hash Input : E5648030E680061232006246
MRZ Hash : 56 17 54 EE 47 DA 42 56 C1 5F E4 F4 0A 17 63 9C B7 5F 4C 26
Value of Key : EB 0F 20 E3 5D F2 9C 76 EC D3 EF 57 4B C7 4A 1D
Hash Input : E5648030E680061232006246
MRZ Hash : 56 17 54 EE 47 DA 42 56 C1 5F E4 F4 0A 17 63 9C B7 5F 4C 26
Value of Key : 6D C3 7B 57 1C 8E 53 DD 1B EA B6 E7 CB 41 85 EC
Performing mutual authentication
Plain Block : 7F 37 6D 71 35 60 3F EB 9E 23 1A F7 C3 A1 91 AD 57 3B C4 51 80 D9 58 6A A9 A7 A8 5B 55 E8 35 8A
Cryptogram : DC 1D F1 38 CD 8D 04 92 DA 04 45 83 28 C9 65 A0 0A F4 78 08 D9 E9 C0 45 15 DE B2 E9 3A F9 6A A4
MAC : B1 5E 3A B4 A2 24 E8 93
Response : 39 83 27 0A AD E2 C6 84 1E 35 8D 62 6C F6 75 71 35 AF F3 76 54 8C 25 0D 95 4F 4B F0 7E 2D 64 30 81 F9 64 E0 E9 BE 66 0D
Plain Block : 9E 23 1A F7 C3 A1 91 AD 7F 37 6D 71 35 60 3F EB A6 E7 6A 1C E3 05 95 F1 AF A5 B3 AD E8 0E 54 FF
Kenc : A9 A5 38 46 BB AD 5D 9F DF E2 5B 58 16 DE 05 AD
Kmac : BA 0C 8B 9F A6 41 87 67 1A 0A 1D B8 CD CD 65 AA
SSC : C3 A1 91 AD 35 60 3F EB
Reading EF_COM (1E)...
Content
0000 60 16 5F 01 04 30 31 30 37 5F 36 06 30 34 30 30 `._..0107_6.0400
0010 30 30 5C 04 61 75 63 6D 00\.aucmWriting E:\Tools\JavaCard\scsh_workspace\EF_COM.bin
Reading EF_DG1 (01)...
Content
0000 61 5B 5F 1F 58 50 41 53 47 50 58 49 4F 4E 47 3C a[_.XPASGPXIONG<
0010 3C 48 55 49 4C 49 4E 3C 3C 3C 3C 3C 3C 3C 3C 3C <HUILIN<<<<<<<<<
0020 3C 3C 3C 3C 3C 3C 3C 3C 3C 3C 3C 3C 3C 3C 3C 3C <<<<<<<<<<<<<<<<
0030 3C 45 35 36 34 38 30 33 30 45 36 53 47 50 38 30 <E5648030E6SGP80
0040 30 36 31 32 33 4D 32 30 30 36 32 34 36 53 38 30 06123M2006246S80
0050 36 33 30 39 39 49 3C 3C 3C 3C 3C 39 32 63099I<<<<<92
......
Check digit
There will be check digit calculation, for example:
Date of birth = 690806, check digit = 1
Refer to Wiki Machine-readable_passport, there is check digit description as below:
The check digit calculation is as follows: each position is assigned a value; for the digits 0 to 9 this is the value of the digits, for the letters A to Z this is 10 to 35, for the filler < this is 0. The value of each position is then multiplied by its weight; the weight of the first position is 7, of the second it is 3, and of the third it is 1, and after that the weights repeat 7, 3, 1, and so on. All values are added together and the remainder of the final value divided by 10 is the check digit.
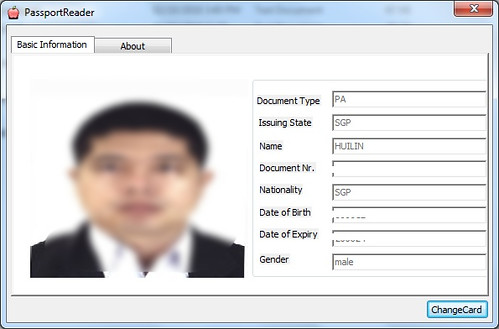
Reading passport using PassportReader
Using another software PassportReader has the same result as below,
Reference
Open SmartCard Biometric Passport (MRTD) with Logical Data Structure (LDS)
Javacardos JMRTD
https://github.com/credentials/scuba
Wiki Machine-readable_passport
Calculate the SHA 1 online
Calculate XOR online
JMRTD: Machine Readable Travel Documents ICAO ePassport API and application SourceForge
Github JMRTD
ICAO doc 9303 part 1 volume 2