bugkuctf 这是一张单纯的图片
描 述: key{}

key{you are right}

key{you are right}
bugkuctf 隐写
描 述: BUGKU{xxxx}


bugkuctf telnet
描 述: key格式flag{xxxxxxxxxxxxxxxxxxxxxxxxxxx}

flag{d316759c281bf925d600be698a4973d5}
bugkuctf 眼见非实
描 述: flag{}
ZIP Archive (zip),文件头:504B0304


flag{F1@g}
bugkuctf 啊哒
描 述: 有趣的表情包 来源:第七届山东省大学生网络安全技能大赛



binwalk -e ada.jpg

flag{3XiF_iNf0rM@ti0n}
bugkuctf ping
描 述: 请输入flag

flag{dc76a1eee6e3822877ed627e0a04ab4a}
bugkuctf 赛博朋克
描 述: flag{}





flag{Hel1o_Wor1e}
bugkuctf 又一张图片,还单纯吗
描 述: 好像和上一个有点不一样
foremost -T file.jpg

falg{NSCTF_e6532a34928a3d1dadd0b049d5a3cc57}
bugkuctf 猜
描 述: flag格式key{图中人物名字全拼}

key{liuyifei}
bugkuctf 宽带信息泄露
描 述: flag{宽带用户名}
RouterPassView

flag{053700357621}
bugkuctf 隐写2
描 述: f1@g{xxx}

binwalk -e welcome.jpg
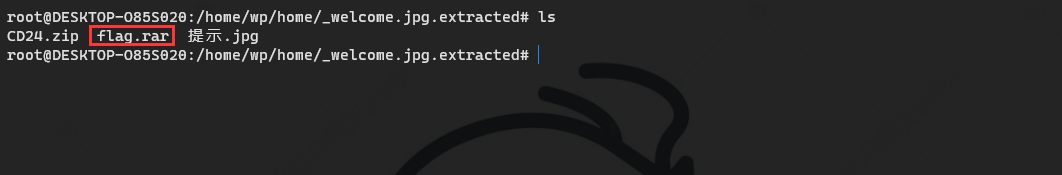
Advanced Archive Password Recovery



f1@g{eTB1IEFyZSBhIGhAY2tlciE=}
bugkuctf 多种方法解决
描 述: 在做题过程中你会得到一个二维码图片


KEY{dca57f966e4e4e31fd5b15417da63269}
bugkuctf 闪的好快
描 述: 这是二维码吗?嗯。。。是二维码了,我靠,闪的好快。。。
题目来源:第七季极客大挑战

SYC{F1aSh_so_f4sT}
bugkuctf come_game
描 述: 听说游戏通关就有flag 题目来源:第七季极客大挑战

按R 回到出生点



SYC{6E23F259D98DF153}
bugkuctf 白哥的鸽子
描 述: 咕咕咕


flag{w22_is_v3ry_cool}
bugkuctf linux
描 述: linux基础问题

key{feb81d3834e2423c9903f4755464060b}
bugkuctf 富强民主
描 述: 公正公正公正诚信文明公正民主公正法治法治友善平等和谐敬业和谐富强和谐富强和谐文明和谐平等公正公正和谐法治公正公正公正文明和谐民主和谐敬业和谐平等和谐敬业和谐敬业和谐和谐和谐公正法治友善法治

flag{90025f7fb1959936}
bugkuctf 放松一下吧
描 述: bugku{}

password:happy_i_wanna

password:????????
贝斯的老大也可以解这个问题

666666

https://github.com/wpsec/F5-steganography
java Extract ../home/-p 66666666

bugku{F5_and_i_wanna_is_so_cool}
bugkuctf cisco
描 述: 密码是flag
Switch>enable
flag
Switch#show running-config

flag{wenzi_houzhui_sike}
bugkuctf 隐写3
描 述: flag{}

flag{He1l0_d4_ba1}
bugkuctf 做个游戏
描 述: 坚持60秒

flag{RGFqaURhbGlfSmlud2FuQ2hpamk=}

flag{DajiDali_JinwanChiji}
bugkuctf 想蹭网先解开密码
描 述: flag格式:flag{你破解的WiFi密码} tips:密码为手机号,为了不为难你,大佬特地让我悄悄地把前七位告诉你 1391040** Goodluck!! 作者@NewBee

flag{13910407686}
bugkuctf zip伪加密
描 述: zip伪加密



flag{Adm1N-B2G-kU-SZIP}
bugkuctf 三色绘恋
描 述: 今天,我问超哥,你会做简单MISC吗?超哥说:那不是有手就行? 你们拥有超哥的手吗?


key is a56v1sa6fc

fLag{M0_XIa0_Ju_T1an_XIa_Dl_1!}
bugkuctf 只有黑棋的棋盘
提 示: 动手修复
描 述: flag{}

ZIP Archive (zip),文件头:504B0304


…
…
CDEFGHIJKLMNOPQRSTU
BCDEFGHIJKLMNOPQRST
ABCDEFGHIJKLMNOPQRS

JKLMNOPQRSTUVWXYZAB
IJKLMNOPQRSTUVWXYZA
HIJKLMNOPQRSTUVWXYZ
GHIJKLMNOPQRSTUVWXY
FGHIJKLMNOPQRSTUVWX
EFGHIJKLMNOPQRSTUVW
DEFGHIJKLMNOPQRSTUV
CDEFGHIJKLMNOPQRSTU
BCDEFGHIJKLMNOPQRST
ABCDEFGHIJKLMNOPQRS
GOODGOPLAY



flag{1t_1s_1nterest1n9}
bugkuctf 蜘蛛侠
描 述: flag{}

〤〤〡十〦〩〩〨十〡

商码:〡 〢 〣 〤 〥 〦 〧 〨 〩 十
汉字:一 二 三 四 五 六 七 八 九 十
大写:壹 贰 叁 肆 伍 陆 柒 捌 玖 拾
数字:1 2 3 4 5 6 7 8 9 10
| 商码 | 数字 |
|---|---|
| 〤 | 4 |
| 〤 | 4 |
| 〡 | 1 |
| 十 | 10 |
| 〦 | 6 |
| 〩 | 9 |
| 〩 | 9 |
| 〨 | 8 |
| 十 | 10 |
| 〡 | 1 |
441106998101
password:肆肆壹拾陆玖玖捌拾壹

# encode.py
import os
data_jpg = open('key.jpg','wb')
def jpg_encode():with open('file.jpg','rb') as handle:size = os.path.getsize('file.jpg')print(size)i = 0while i<size:bytedata = handle.read(1)process_data = data_encode(bytedata)data_write(process_data)i = i + 1def data_encode(bytedata):data = int.from_bytes(bytedata,byteorder='big')if (data % 2 == 0):data = (data + 1) ^ 128else:data = (data - 1) ^ 128data = bytes([data])return datadef data_write(process_data):data_jpg.write(process_data)if __name__ == '__main__':jpg_encode()data_jpg.close()
import os# data_jpg = open('key.jpg', 'wb')
data_jpg = open("file.jpg", "wb")def jpg_encode():with open('file.jpg', 'rb') as handle:size = os.path.getsize('file.jpg')print(size)i = 0while i < size:bytedata = handle.read(1)process_data = data_encode(bytedata)data_write(process_data)i = i + 1def jpg_decode():with open("key.jpg", "rb") as handle:size = os.path.getsize("key.jpg")print(size)i = 0while i < size:ByteData = handle.read(1)process_data = data_decode(ByteData)data_write(process_data)i = i + 1def data_decode(bytedata):try:data = int.from_bytes(bytedata, byteorder='big')if data % 2 == 0:data = (data ^ 128) + 1else:data = (data ^ 128) - 1data = bytes([data])return dataexcept ValueError as ve:print(ve)def data_encode(bytedata):data = int.from_bytes(bytedata, byteorder='big')if (data % 2 == 0):data = (data + 1) ^ 128else:data = (data - 1) ^ 128data = bytes([data])return datadef data_write(process_data):data_jpg.write(process_data)if __name__ == '__main__':jpg_decode()data_jpg.close()



password:SilentEye

flag{spider-man_is_really_cool}